Actualizado el 09/07/2025
1 in 3 automotive cyber incidents result in car theft or break-insEscrito por Redacción TNI el 22/02/2022 a las 21:08:171447
 A steady trend toward connected, autonomous, shared, and electric vehicles have effectively transformed automobiles into mobile computing platforms on wheels, allowing for a better consumer and ownership experience.
However, because of these advances, many new cyberattack vectors have appeared. All of these technologies, including keyless entry, remote start, remote shut down, and mobile applications for cars, can be used as intrusion points.
Moreover, automotive cyber-attacks are potentially more harmful than cyber attacks on computer or phone devices since they can physically put the victim in danger.
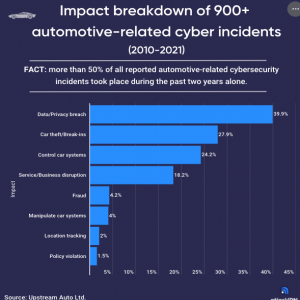
So, in reality, how concerning are automotive-related cyber incidents? We can find the answer in the recently published data by Upstream Security Ltd. The team analyzed over 900 automotive cyber-incidents from 2010 until the end of 2021, revealing that the most common result of auto cyber-attacks is a data or a privacy breach.
According to the findings, nearly 40% of incidents in the past twelve years caused victims' identities to be exposed in one way or another. Depending on the severity of the leak, information revealed in a data breach can be as simple as an email address or as sensitive as credit card details. You can read our article on the data that your car stores about you here.
Perhaps more concerning is the second-most common result of an automotive cyber incident: nearly a third (27.9%) of them result in car theft or a break-in.
Many expect top-notch security when purchasing a vehicle with advanced technologies, but cybercriminals can take advantage of those systems.
Third on the list, with 24.2%, is the control of car systems. Meaning nearly a fourth of intrusions enabled hackers to control the majority if not all functions within the vehicle.
This is also one of the more distressing findings since it can endanger the driver and passengers if they are in a moving car at the time of the incident.
With the introduction of autonomous driving, it is uncomfortable to contemplate how far criminals could take such car-system control take-overs.
Almost a thousand incidents in more than ten years are no reason for drivers to be paranoid. Yet, the worrying fact is that more than 50% of all reported automotive-related cybersecurity incidents took place during the past two years alone.
Most common attack vectors
We know the most common results of automotive-related cyber incidents, but it is also worth understanding the road cybercriminals take to carry out these attacks.
There are several attack vectors for connected vehicles. However, some are more common than others. The figures of automotive cyber incident attack vectors are depicted in the graph below.
Over 40% of cyber attacks were carried out by hacking into the servers. While it might not seem like a big deal at first glance, hacking into OEMs’ servers is significant.
Most OEMs' servers are in charge of command and control services. This means they can operate vehicle operations remotely by sending commands like “lock” and “unlock” to a car's doors, start the engine, and more.
As a result, if these servers are hacked, drivers and passengers may be at risk.
Moving on to the next most common attack vector, we see keyless entry or key fob at 26.3%.
It’s not surprising that fraudsters focus on methods that provide entrance into the car since their attacks are nearly always financially motivated. Even if they are unable to steal the vehicle itself, they can run off with car equipment or the victims' personal belongings.
In the third spot on the list of most common attack vectors, we see Electronic Control Units (ECUs) and Telematics Control Units (TCUs) at 12.2%.
While ECU is self-explanatory, TCU refers to the embedded system on a vehicle that connects it to the telematics server, enabling vehicle tracking, telemetry collection, remote commands, and additional services.
Mobile applications (7.3%) and infotainment systems (5.7%) also make the top 5 list of the most common intrusion points into connected vehicles.
We want to conclude the findings with a quote from the CEO of Jaguar Land Rover, Sir Ralf D Speth:
“In a connected world, cybersecurity is as fundamental to your safety as the brakes.”
|